Recent Research Themes
Classification of Fake Contents
By using deep learning technology with multiple videos of a person as supervised data, it is possible to create fake contents that realistically reproduce false statements. It has been pointed out that if this technology is misused to create fake content and spread it over the Internet, it could have a significant impact. In order to cope with this problem, it is necessary to develop a technology to determine "artificially created contents" and "normal content". In this research, we aim to develop a system to classify whether or not the target content has been created by artificial processing.
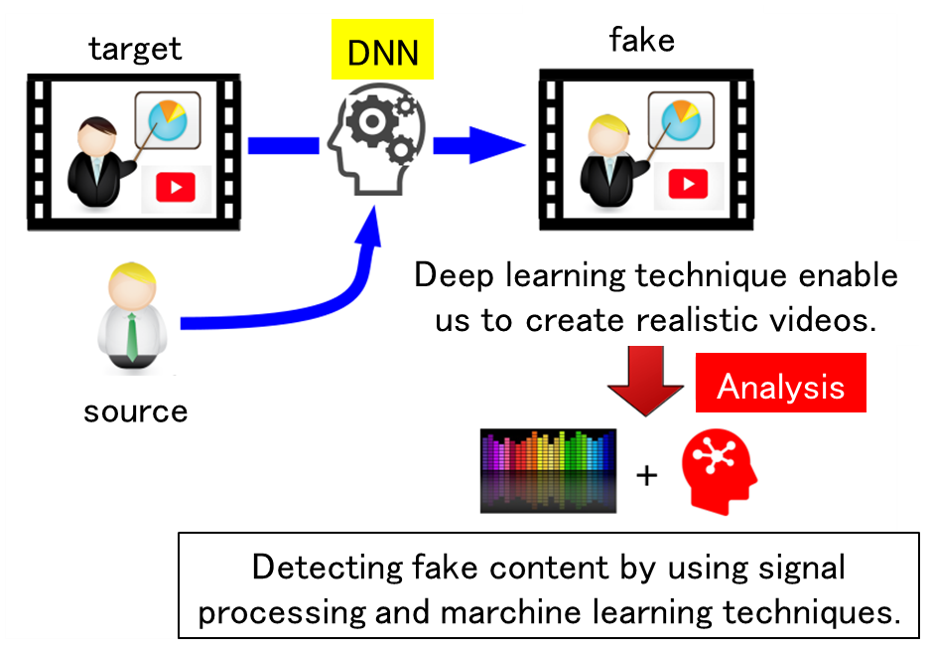
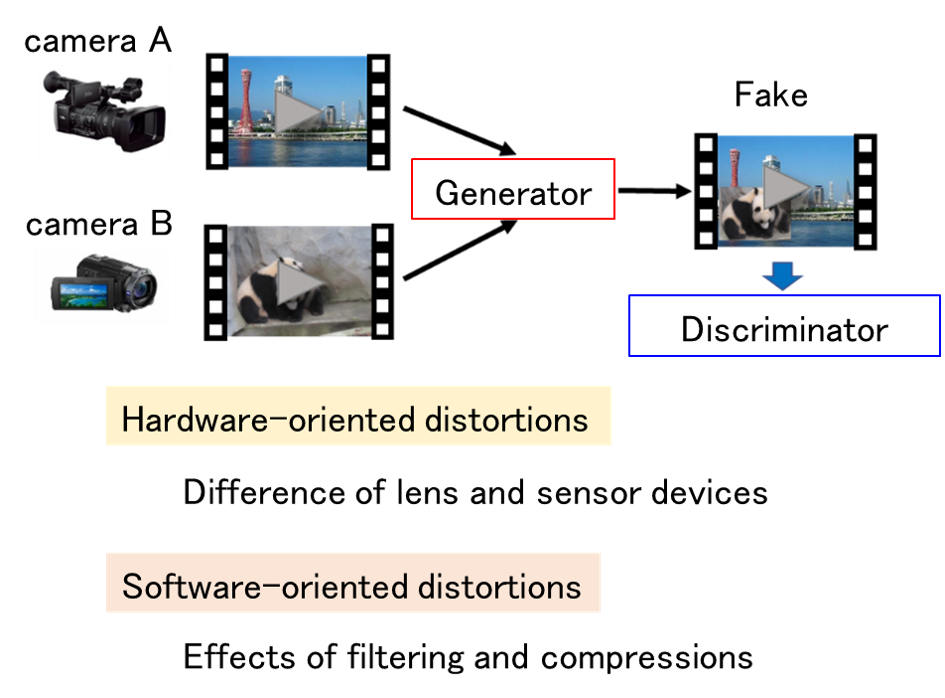 Related results
A. Malik, M. Kuribayashi, S. M. Abdullahi, A. N. Khan,
"DeepFake Detection for Human Face Images and Videos: A Survey,"
IEEE Access, vol.10, pp.18757-18775, 2022.
K. Kamakari, M. Kuribayashi, N. Funabiki,
"A Study of Countermeasures against Information Leakage by Screen Capture on Online Meeting System,"
The 2022 Symp. on Cryptography and Information Security (SCIS2022), 2022. (in Japanese)
A. Qureshi, D. Megias, M. Kuribayashi,
"Detecting deepfake videos using digital watermarking,"
Asia-Pacific Signal and Information Processing Association Anual Sumit and Conf. (APSIPA ASC 2021), pp.1786-1793, 2021.
D. Takeshita, M. Kuribayashi, N. Funabiki,
"A study of feature extraction suitable for double JPEG compression analysis based on statistical bias observation of DCT coefficients,"
Asia-Pacific Signal and Information Processing Association Anual Sumit and Conf. (APSIPA ASC 2021), pp.1808-1814, 2021.
K. Nakai, M. Kuribayashi, N. Funabiki,
"A study of privacy protection of photos taken by wide-angle surveillance camera,"
Asia-Pacific Signal and Information Processing Association Anual Sumit and Conf. (APSIPA ASC 2021), pp.1865-1871, 2021.
D. Takeshita, M. Kuribayashi, N. Funabiki,
"A study on feature extraction suitable for double JPEG compression analysis based on statistical bias observation of DCT coefficients,"
Technical Report of IEICE, EMM May, 2021. (in Japanese)
K. Kawata, M. Kuribayashi, N. Funabiki,
"Deep fake video detection based on pre-trained CNN models with fine-tuning focusing on face regions,"
The 2021 Symp. on Cryptography and Information Security (SCIS2021), 2021. (in Japanese)
M. Kuribayashi, K. Kamakari, K. Kawata, N. Funabiki,
"Classification of video recaptured from display device,"
Proc. APSIPA ASC 2020, pp.1381-1385, 2020.
N. Nakajima, M. Kuribayashi, N. Funabiki,
"Evaluation on JPEG image compression history analysis using histogram of DCT coefficients with different block size,"
Technical Report of IEICE, EMM Nov., 2020. (in Japanese)
K. Oura, M. Kuribayashi, N. Funabiki,
"CNN-based analysis on editing history of JPEG file using histogram of DCT coefficients,"
Technical Report of IEICE, EMM March, 2020. (in Japanese)
K. Kamakari, K. Kawata, M. Kuribayashi, N. Funabiki,
"Detection of illegal movies captured by video camera from display device,"
Technical Report of IEICE, EMM March, 2020. (in Japanese)
K. Oura, M. Kuribayashi, N. Funabiki,
"Analysis on editing history of JPEG file based on the bias in histogram of DCT coefficients,"
Computer Security Symposium 2019, 2019. (in Japanese)
Related results
A. Malik, M. Kuribayashi, S. M. Abdullahi, A. N. Khan,
"DeepFake Detection for Human Face Images and Videos: A Survey,"
IEEE Access, vol.10, pp.18757-18775, 2022.
K. Kamakari, M. Kuribayashi, N. Funabiki,
"A Study of Countermeasures against Information Leakage by Screen Capture on Online Meeting System,"
The 2022 Symp. on Cryptography and Information Security (SCIS2022), 2022. (in Japanese)
A. Qureshi, D. Megias, M. Kuribayashi,
"Detecting deepfake videos using digital watermarking,"
Asia-Pacific Signal and Information Processing Association Anual Sumit and Conf. (APSIPA ASC 2021), pp.1786-1793, 2021.
D. Takeshita, M. Kuribayashi, N. Funabiki,
"A study of feature extraction suitable for double JPEG compression analysis based on statistical bias observation of DCT coefficients,"
Asia-Pacific Signal and Information Processing Association Anual Sumit and Conf. (APSIPA ASC 2021), pp.1808-1814, 2021.
K. Nakai, M. Kuribayashi, N. Funabiki,
"A study of privacy protection of photos taken by wide-angle surveillance camera,"
Asia-Pacific Signal and Information Processing Association Anual Sumit and Conf. (APSIPA ASC 2021), pp.1865-1871, 2021.
D. Takeshita, M. Kuribayashi, N. Funabiki,
"A study on feature extraction suitable for double JPEG compression analysis based on statistical bias observation of DCT coefficients,"
Technical Report of IEICE, EMM May, 2021. (in Japanese)
K. Kawata, M. Kuribayashi, N. Funabiki,
"Deep fake video detection based on pre-trained CNN models with fine-tuning focusing on face regions,"
The 2021 Symp. on Cryptography and Information Security (SCIS2021), 2021. (in Japanese)
M. Kuribayashi, K. Kamakari, K. Kawata, N. Funabiki,
"Classification of video recaptured from display device,"
Proc. APSIPA ASC 2020, pp.1381-1385, 2020.
N. Nakajima, M. Kuribayashi, N. Funabiki,
"Evaluation on JPEG image compression history analysis using histogram of DCT coefficients with different block size,"
Technical Report of IEICE, EMM Nov., 2020. (in Japanese)
K. Oura, M. Kuribayashi, N. Funabiki,
"CNN-based analysis on editing history of JPEG file using histogram of DCT coefficients,"
Technical Report of IEICE, EMM March, 2020. (in Japanese)
K. Kamakari, K. Kawata, M. Kuribayashi, N. Funabiki,
"Detection of illegal movies captured by video camera from display device,"
Technical Report of IEICE, EMM March, 2020. (in Japanese)
K. Oura, M. Kuribayashi, N. Funabiki,
"Analysis on editing history of JPEG file based on the bias in histogram of DCT coefficients,"
Computer Security Symposium 2019, 2019. (in Japanese)
Detection of Adversarial Examples
Convolutional neural networks (CNNs) have been applied to image recognition in many research fields such as face recognition and automatic driving. However, there is a problem that it is possible to make the CNN image recognition system detect false positives by intentionally adding noise. This problem is called adversarial examples, and it is an unavoidable characteristic of machine learning classifiers. In this research, we aim to protect the integrity of the machine learning system by preprocessing the image input to the image recognition system to classify whether it is a normal image or an adversarial case with intentional noise.
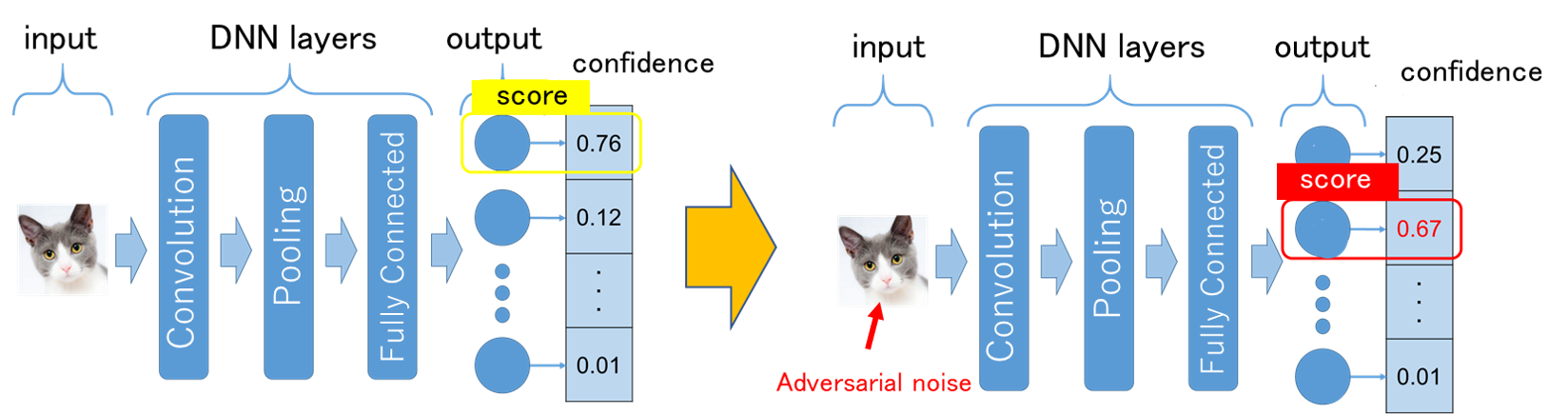
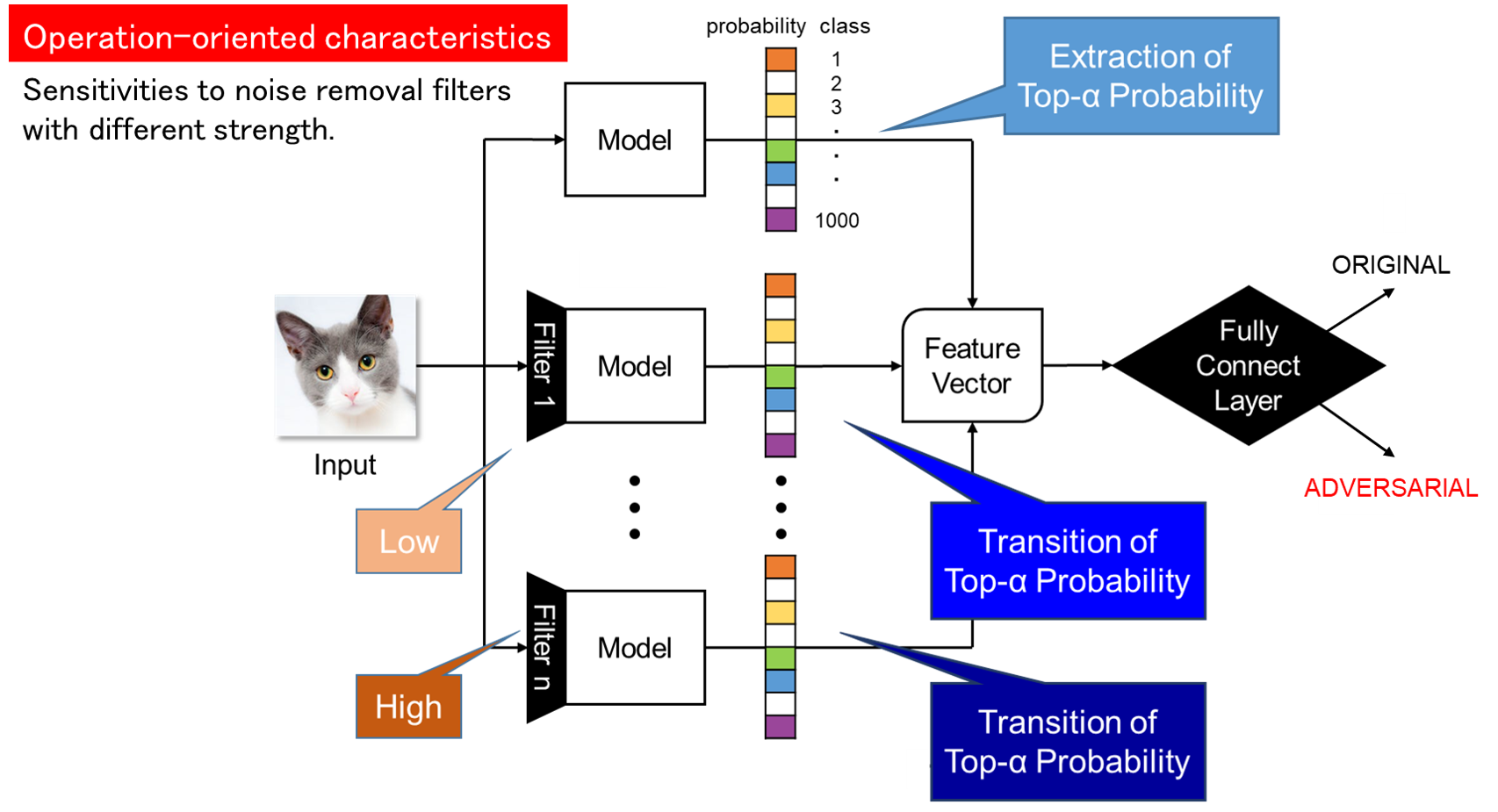 Related results
H. H. Nguyen, M. Kuribayashi, J. Yamagishi, I. Echizen,
"Effects of Image Processing Operations on Adversarial Noise and Their Use in Detecting and Correcting Adversarial Images,"
IEICE Trans. Inf. Syst., vol.E105-D, no.1, pp.65-77, 2022. 2022 IEICE Best Paper Award
K. Tsunomori, Y. Yamasaki, M. Kuribayashi, N. Funabiki, I. Echizen,
"Detection of Adversarial Examples Using Sensitivities to JPEG Compression-Derived Signals,"
The 2022 Symp. on Cryptography and Information Security (SCIS2022), 2022. (in Japanese)
Y. Yamasaki, M. Kuribayashi, N. Funabiki, H. H. Nguyen, I. Echizen,
"A study of feature extraction based on denoising auto encoder for classification of adversarial examples,"
Asia-Pacific Signal and Information Processing Association Anual Sumit and Conf. (APSIPA ASC 2021), pp.1815-1820, 2021.
Y. Yamasaki, M. Kuribayashi, N. Funabiki, H. H. Nguyen, I. Echizen,
"A study of detecting adversarial examples using sensitivities to multiple auto encoders,"
Technical Report of IEICE, EMM May, 2021. (in Japanese)
A. Higashi, M. Kuribayashi, N. Funabiki, H. H. Nguyen, I. Echizen,
"Detection of adversarial examples in CNN image classifiers using features extracted with multiple strengths of filter,"
Technical Report of IEICE, EMM March, 2021. (in Japanese)
6th Workshop Best Student Presentation Award
A. Higashi, M. Kuribayashi, N. Funabiki, H. H. Nguyen, I. Echizen,
"Detection of adversarial examples based on sensitivities to noise removal filter,"
Proc. APSIPA ASC 2020, pp.1386-1391, 2020.
A. Higashi, M. Kuribayashi, N. Funabiki, H. H. Nguyen, I. Echizen,
"Detecting adversarial examples based on sensitivities to lossy compression algorithms,"
Technical Report of IEICE, EMM March, 2020. (in Japanese)
A. Higashi, M. Kuribayashi, N. Funabiki, H. H. Nguyen, I. Echizen,
"Detecting adversarial example based on changes of CNN classication results caused by JPEG compression,"
Computer Security Symposium 2019, 2019. (in Japanese)
PWS2019 Student Best Paper Award
Related results
H. H. Nguyen, M. Kuribayashi, J. Yamagishi, I. Echizen,
"Effects of Image Processing Operations on Adversarial Noise and Their Use in Detecting and Correcting Adversarial Images,"
IEICE Trans. Inf. Syst., vol.E105-D, no.1, pp.65-77, 2022. 2022 IEICE Best Paper Award
K. Tsunomori, Y. Yamasaki, M. Kuribayashi, N. Funabiki, I. Echizen,
"Detection of Adversarial Examples Using Sensitivities to JPEG Compression-Derived Signals,"
The 2022 Symp. on Cryptography and Information Security (SCIS2022), 2022. (in Japanese)
Y. Yamasaki, M. Kuribayashi, N. Funabiki, H. H. Nguyen, I. Echizen,
"A study of feature extraction based on denoising auto encoder for classification of adversarial examples,"
Asia-Pacific Signal and Information Processing Association Anual Sumit and Conf. (APSIPA ASC 2021), pp.1815-1820, 2021.
Y. Yamasaki, M. Kuribayashi, N. Funabiki, H. H. Nguyen, I. Echizen,
"A study of detecting adversarial examples using sensitivities to multiple auto encoders,"
Technical Report of IEICE, EMM May, 2021. (in Japanese)
A. Higashi, M. Kuribayashi, N. Funabiki, H. H. Nguyen, I. Echizen,
"Detection of adversarial examples in CNN image classifiers using features extracted with multiple strengths of filter,"
Technical Report of IEICE, EMM March, 2021. (in Japanese)
6th Workshop Best Student Presentation Award
A. Higashi, M. Kuribayashi, N. Funabiki, H. H. Nguyen, I. Echizen,
"Detection of adversarial examples based on sensitivities to noise removal filter,"
Proc. APSIPA ASC 2020, pp.1386-1391, 2020.
A. Higashi, M. Kuribayashi, N. Funabiki, H. H. Nguyen, I. Echizen,
"Detecting adversarial examples based on sensitivities to lossy compression algorithms,"
Technical Report of IEICE, EMM March, 2020. (in Japanese)
A. Higashi, M. Kuribayashi, N. Funabiki, H. H. Nguyen, I. Echizen,
"Detecting adversarial example based on changes of CNN classication results caused by JPEG compression,"
Computer Security Symposium 2019, 2019. (in Japanese)
PWS2019 Student Best Paper Award
Watermarking for DNN Model
In order to efficiently develop systems based on deep learning using neural networks, it is important to share DNN models that have been trained using big data. To create such trained models, a lot of processing power and a huge amount of dataset are required. The weights of the trained models are of great value, and it is necessary to prevent the models from being easily copied and misused. In this research, we address this problem by embedding a watermark during training of DNN models. Unlike multimedia content such as images, video, and audio signals, we aim to realize a method that cannot be easily removed while minimizing the performance degradation of DNN models by embedding watermark information.
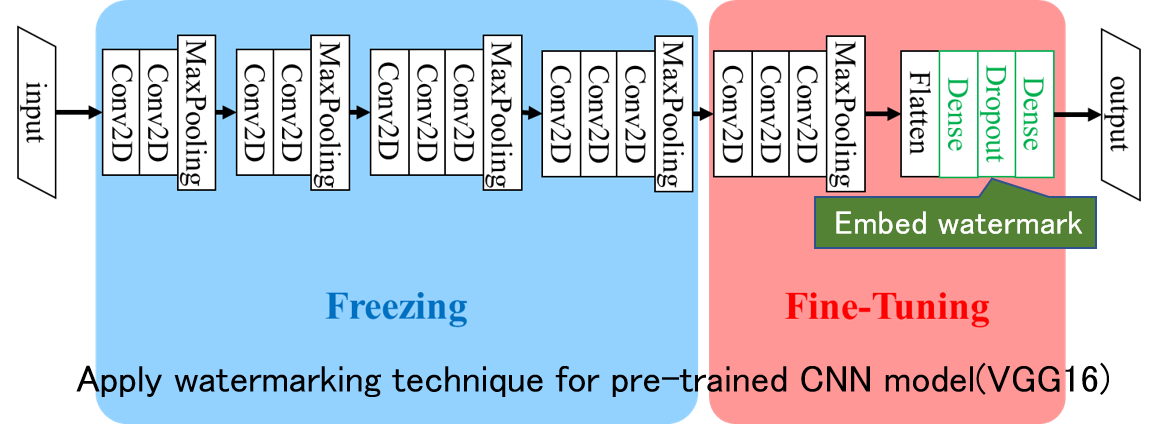 Related results
T. Yasui, T. Tanaka, A. Malik, M. Kuribayashi,
"Coded DNN watermark: robustness against pruning models using constant weight code,"
Journal of Imaging, vol.8, no.6, 16pages, 2022.
M. Kuribayashi, T. Tanaka, S. Suzuki, T. Yasui, and Nobuo Funabiki,
"White-box watermarking scheme for fully-connected layers in fine-tuning model,"
9th ACM Workshop on Information Hiding and Multimedia Security (IH&MMSec'21), pp.165-170, 2021.
M. Kuribayashi, T. Tanaka, Nobuo Funabiki,
"DeepWatermark: embedding watermark into DNN model,"
Proc. APSIPA ASC 2020, pp.1340-1346, 2020.
T. Tanaka, M. Kuribayashi, N. Funabiki,
"DM-QIM watermarking for fully connected layers of DNN model,"
Technical Report of IEICE, EMM Sept., 2020. (in Japanese)
2020 EMM Best Student Paper Award
T. Tanaka, T. Yasui, M. Kuribayashi, N. Funabiki,
"DM-QIM watermarking for weights of deep neural network,"
Technical Report of IEICE, EMM March, 2020. (in Japanese)
Related results
T. Yasui, T. Tanaka, A. Malik, M. Kuribayashi,
"Coded DNN watermark: robustness against pruning models using constant weight code,"
Journal of Imaging, vol.8, no.6, 16pages, 2022.
M. Kuribayashi, T. Tanaka, S. Suzuki, T. Yasui, and Nobuo Funabiki,
"White-box watermarking scheme for fully-connected layers in fine-tuning model,"
9th ACM Workshop on Information Hiding and Multimedia Security (IH&MMSec'21), pp.165-170, 2021.
M. Kuribayashi, T. Tanaka, Nobuo Funabiki,
"DeepWatermark: embedding watermark into DNN model,"
Proc. APSIPA ASC 2020, pp.1340-1346, 2020.
T. Tanaka, M. Kuribayashi, N. Funabiki,
"DM-QIM watermarking for fully connected layers of DNN model,"
Technical Report of IEICE, EMM Sept., 2020. (in Japanese)
2020 EMM Best Student Paper Award
T. Tanaka, T. Yasui, M. Kuribayashi, N. Funabiki,
"DM-QIM watermarking for weights of deep neural network,"
Technical Report of IEICE, EMM March, 2020. (in Japanese)
Data Hiding for PDF files
Watermarking technology has mainly dealt with digital content such as images, videos, audio, etc. On the other hand, in digital libraries and information distribution services for office documents, most of the leaked content are electronic documents. In this research, we focus on PDF files, which are widely used as a de facto standard, and apply watermarking technology to them by making good use of their file structure.
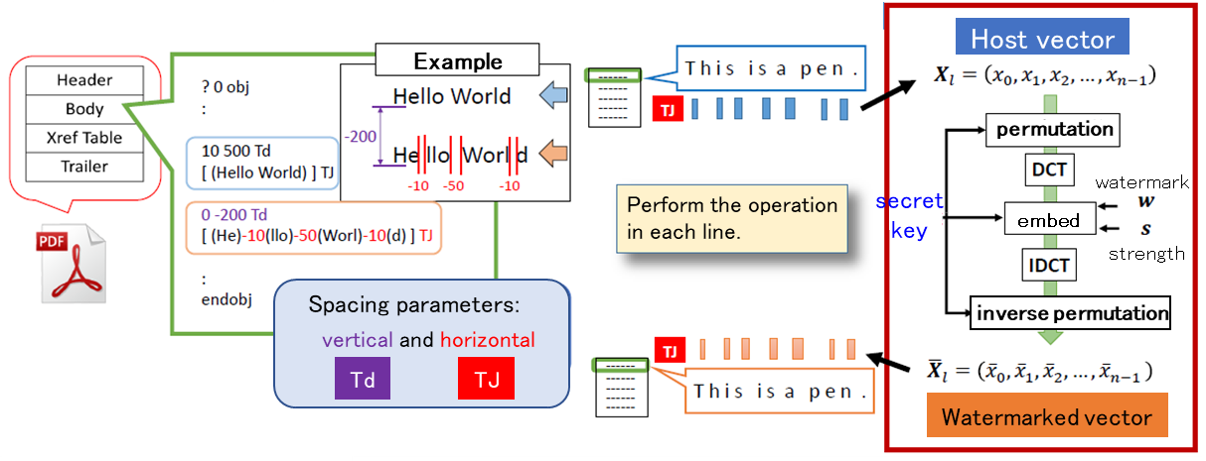 Related results
M. Kuribayashi and K.S. Wong,
"StealthPDF: Data hiding method for PDF file with no visual degradation,"
Journal of Information Security and Applications, vol.61, no.102875, 10pages, 2021.
M. Kuribayashi and K. S. Wong,
"Improved DM-QIM watermarking scheme for PDF document,"
Proc. IWDW2019, LNCS 12022, pp.171-183, Springer-Verlag, 2019.
Best Paper Award
N. Nursiah, K. S. Wong, and M. Kuribayashi,
"Reversible data hiding in PDF document exploiting prefix zeros in glyph coordinates,"
Proc. APSIPA ASC 2019, pp.1298-1302, 2019.
M. Kuribayashi, T. Fukushima, and N. Funabiki,
"Robust and secure data hiding for PDF text document,"
IEICE Trans. Information and Systems, vol.E102-D, no.1, pp.41-47, 2019.
M. Kuribayashi, T. Fukushima, and N. Funabiki,
"Data hiding for text document in PDF file,"
Proc. IIHMSP2017, pp.390-398, 2017.
Excellent Paper Award
T. Fukushima, M. Kuribaysahi, and N. Funabiki,
"Segment-wise watermarking scheme for PDF document file considering the applicability to fingerprinting system,"
Technical Report of IEICE, EMM Nov., 2018. (in Japanese)
T. Fukushima, M. Kuribayashi, and N. Funabiki,
"Imperceptible watermarking scheme with large capacity considering the internal structure of PDF file,"
IWSEC2017, Poster Session, 2017.
T. Fukushima, M. Kuribaysahi, and N. Funabiki,
"Watermarking scheme with large capacity considering the internal structure of PDF file,"
Technical Report of IEICE, EMM May, 2017. (in Japanese)
2017 EMM Best Student Paper Award
Related results
M. Kuribayashi and K.S. Wong,
"StealthPDF: Data hiding method for PDF file with no visual degradation,"
Journal of Information Security and Applications, vol.61, no.102875, 10pages, 2021.
M. Kuribayashi and K. S. Wong,
"Improved DM-QIM watermarking scheme for PDF document,"
Proc. IWDW2019, LNCS 12022, pp.171-183, Springer-Verlag, 2019.
Best Paper Award
N. Nursiah, K. S. Wong, and M. Kuribayashi,
"Reversible data hiding in PDF document exploiting prefix zeros in glyph coordinates,"
Proc. APSIPA ASC 2019, pp.1298-1302, 2019.
M. Kuribayashi, T. Fukushima, and N. Funabiki,
"Robust and secure data hiding for PDF text document,"
IEICE Trans. Information and Systems, vol.E102-D, no.1, pp.41-47, 2019.
M. Kuribayashi, T. Fukushima, and N. Funabiki,
"Data hiding for text document in PDF file,"
Proc. IIHMSP2017, pp.390-398, 2017.
Excellent Paper Award
T. Fukushima, M. Kuribaysahi, and N. Funabiki,
"Segment-wise watermarking scheme for PDF document file considering the applicability to fingerprinting system,"
Technical Report of IEICE, EMM Nov., 2018. (in Japanese)
T. Fukushima, M. Kuribayashi, and N. Funabiki,
"Imperceptible watermarking scheme with large capacity considering the internal structure of PDF file,"
IWSEC2017, Poster Session, 2017.
T. Fukushima, M. Kuribaysahi, and N. Funabiki,
"Watermarking scheme with large capacity considering the internal structure of PDF file,"
Technical Report of IEICE, EMM May, 2017. (in Japanese)
2017 EMM Best Student Paper Award
Secure Management System of Office Documents
With the digitization of document files, countermeasures against unauthorized processing have become an urgent issue. Countermeasures against information leaks and tampering have been important for a long time, and the application of cryptography has been used as the main means. However, in the case of leaks due to internal crimes, the use of advanced cryptographic processing is not effective against criminals who have decryption keys. In this research, we aim to realize a system that automatically stores browsing history in files for users with access privileges.
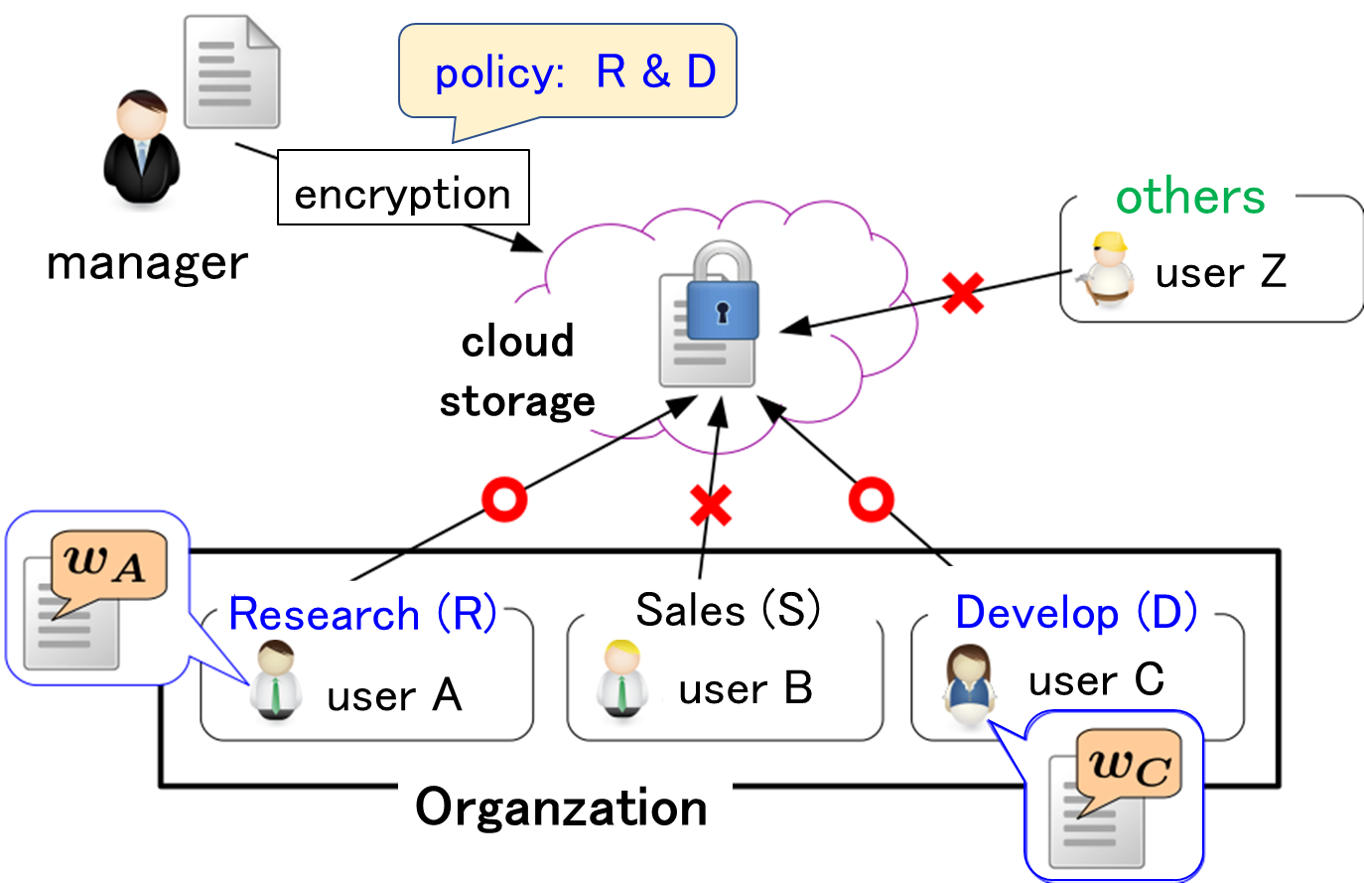 Related results
M. Kuribayashi and N. Funabiki,
"Efficient decentralized tracing protocol for fingerprinting system with index table,"
Proc. APSIPA ASC 2019, pp.1595-1601, 2019.
M. Kuribayashi and N. Funabiki,
"Decentralized tracing protocol for fingerprinting system,"
APSIPA Trans. Signal and Information Processing, vol.8, 8 pages, 2019.
M. Kuribayashi and N. Funabiki,
"Fingerprinting for multimedia content broadcasting system,"
J. Information Security and Applications, vol.41, pp.52-61, 2018.
T. Ueda, M. Kuribayashi, and N. Funabiki,
"Implementation and evaluation of fingerprinting system for preventing internal leakage of sensitive data,"
Technical Report of IEICE, EMM Nov., 2017. (in Japanese)
T. Ueda, M. Kuribayashi, and N. Funabiki,
"Fingerprinting system for secure manegement of sensitive data,"
IWSEC2017, Poster Session, 2017.
T. Ueda, M. Kuribayashi, and N. Funabiki,
A Proposal of Fingerprinting System for Protection of Sensitive Data from Internal Leakage
Technical Report of IEICE, EMM May, 2017. (in Japanese)
Related results
M. Kuribayashi and N. Funabiki,
"Efficient decentralized tracing protocol for fingerprinting system with index table,"
Proc. APSIPA ASC 2019, pp.1595-1601, 2019.
M. Kuribayashi and N. Funabiki,
"Decentralized tracing protocol for fingerprinting system,"
APSIPA Trans. Signal and Information Processing, vol.8, 8 pages, 2019.
M. Kuribayashi and N. Funabiki,
"Fingerprinting for multimedia content broadcasting system,"
J. Information Security and Applications, vol.41, pp.52-61, 2018.
T. Ueda, M. Kuribayashi, and N. Funabiki,
"Implementation and evaluation of fingerprinting system for preventing internal leakage of sensitive data,"
Technical Report of IEICE, EMM Nov., 2017. (in Japanese)
T. Ueda, M. Kuribayashi, and N. Funabiki,
"Fingerprinting system for secure manegement of sensitive data,"
IWSEC2017, Poster Session, 2017.
T. Ueda, M. Kuribayashi, and N. Funabiki,
A Proposal of Fingerprinting System for Protection of Sensitive Data from Internal Leakage
Technical Report of IEICE, EMM May, 2017. (in Japanese)
Designing 2D Codes and its Application
A standard 2D code consists of only black and white modules, and its appearance is a random pattern. On the other hand, it is possible to display images such as logos on 2D codes by changing the error correction function and the shape of the modules. In this study, we are developing an application to create 2D codes that can be read by normal applications while maintaining the quality of the displayed image by changing the coding function of the error correction code. In order to insert a 2D code into an image without much degradation in image quality, we devised a coding method that avoids visually important parts of the code and does not change the structure of the normal code.
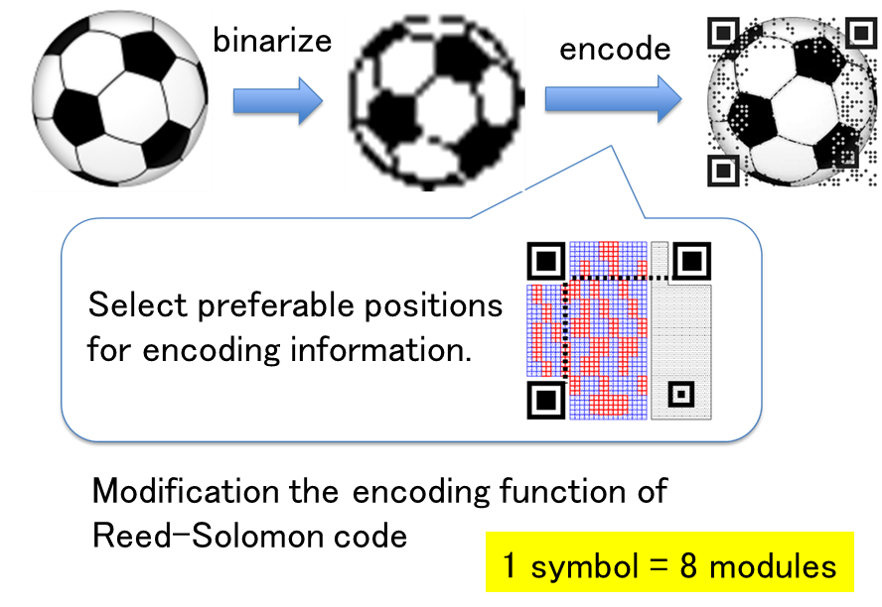
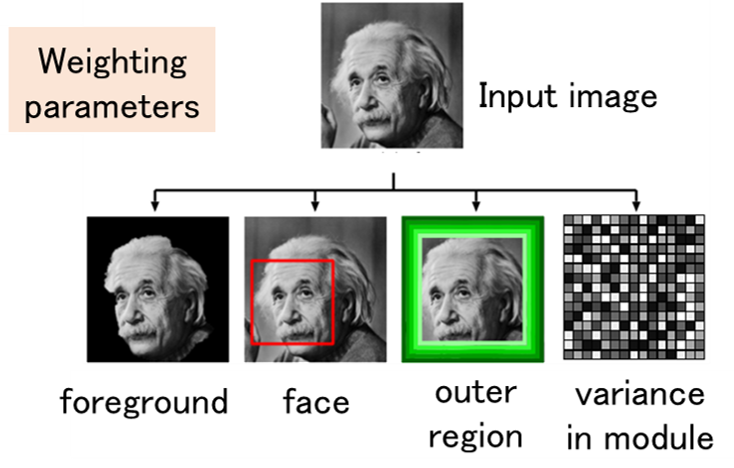
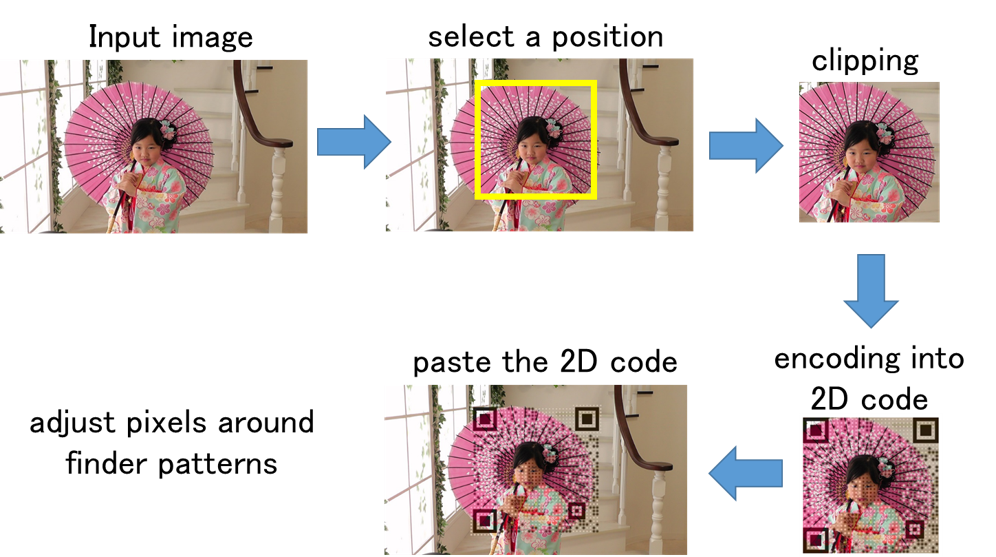 Related results
M. Kuribayashi, G. Murakami, and N. Funabiki,
"A study of aesthetic QR code considering local characteristic of image,"
Technical Report of IEICE, EMM May, 2018. (in Japanese)
M. Kuribayashi and M. Morii,
"Aesthetic QR code based on modified systematic encoding function,"
IEICE Trans. Information and Systems, vol.E100-D, no.1, pp.42-51, 2017.
M. Kuribayashi, E.-C. Chang and N. Funabiki,
"Watermarking with fixed decoder for aesthetic 2D barcode,"
Pro. IWDW2016, LNCS 10082, pp.379-392, Springer-Verlag, 2017.
M. Gyoji, M. Kuribayashi, E.-C. Chang, N. Funabiki,
Development of aesthetic QR code encoder for arbitrary image,"
Technical Report of IEICE, EMM Nov., 2016. (in Japanese)
M. Kuribayashi and M. Morii,
"Enrichment of visual appearance of aesthetic QR code,"
Proc. IWDW2015, LNCS 9569, Springer-Verlag, pp.220-231, 2015.
Related results
M. Kuribayashi, G. Murakami, and N. Funabiki,
"A study of aesthetic QR code considering local characteristic of image,"
Technical Report of IEICE, EMM May, 2018. (in Japanese)
M. Kuribayashi and M. Morii,
"Aesthetic QR code based on modified systematic encoding function,"
IEICE Trans. Information and Systems, vol.E100-D, no.1, pp.42-51, 2017.
M. Kuribayashi, E.-C. Chang and N. Funabiki,
"Watermarking with fixed decoder for aesthetic 2D barcode,"
Pro. IWDW2016, LNCS 10082, pp.379-392, Springer-Verlag, 2017.
M. Gyoji, M. Kuribayashi, E.-C. Chang, N. Funabiki,
Development of aesthetic QR code encoder for arbitrary image,"
Technical Report of IEICE, EMM Nov., 2016. (in Japanese)
M. Kuribayashi and M. Morii,
"Enrichment of visual appearance of aesthetic QR code,"
Proc. IWDW2015, LNCS 9569, Springer-Verlag, pp.220-231, 2015.
Digital Fingerprinting
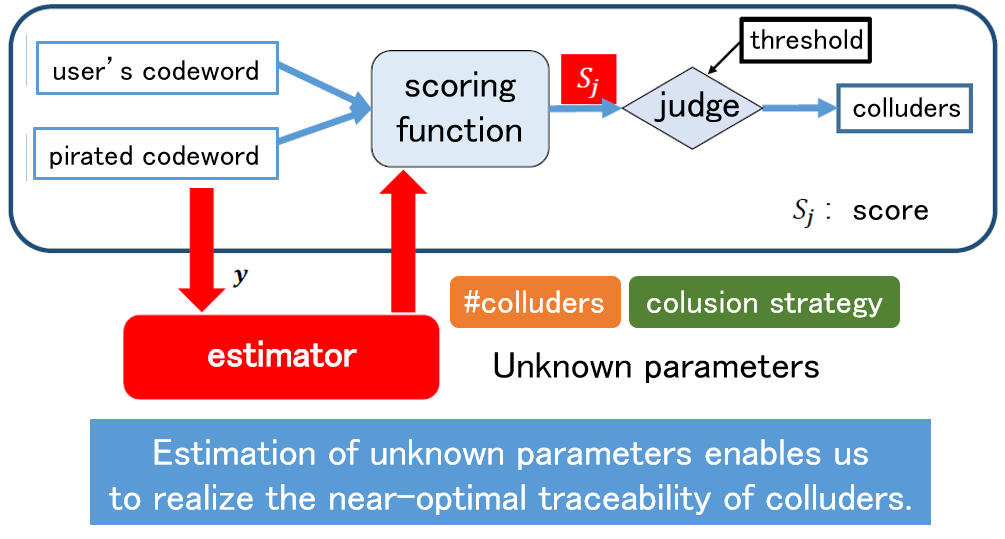
As a countermeasure against unauthorized copying, digital fingerprinting is a method of embedding different identification information in each piece of content using digital watermarking technology when the content is distributed to multiple users. If this identification information is correctly extracted when unauthorized copying is detected, the user who made the unauthorized copy can be uniquely identified. On the other hand, if a coalition of users compares their contents and analyzes the differences, it may not be possible to correctly identify the colluders. Such an attack is called a collusion attack, and collusion-resistant codes have been devised as a countermeasure. Since the publication of a code construction method with the theoretically shortest code length, attention has been focused on decoding methods to identify the collders, and theoretically optimal decoding methods have been devised. In this research, we use signal processing and machine learning techniques to achieve parameter estimation of collusion attacks from signals extracted from an illegal copy, and to obtain properties that are very close to the optimal decoding method.
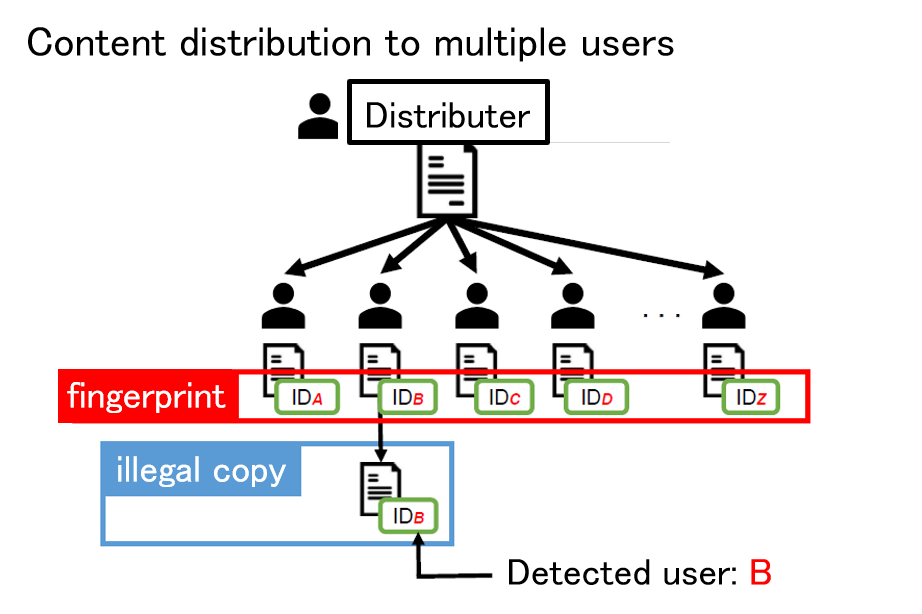
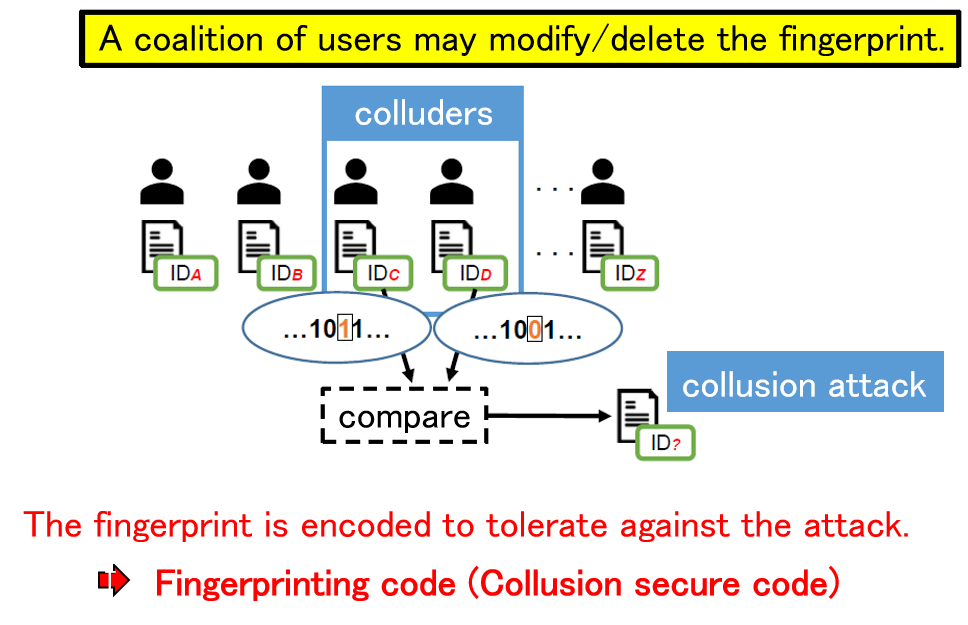
 Related results
T. Yasui, M. Kuribayashi, N. Funabiki, and I. Echizen,
"Near-optimal detector for binary Tardos code by estimating collusion strategy"
IEEE Trans. Information Forensics and Security, vol.15, pp.2069-2080, 2020.
The Telecommunications Advancement Foundation Student Award
T. Yasui, M. Kuribayashi, and N. Funabiki,
"Estimation of collusion strategy for fingerprinting codes under noisy environment,"
Technical Report of IEICE, EMM March, 2019. 2018 EMM Best Poster Award
M. Kuribayashi, "Bias-based binary fingerprinting code under erasure channel,"
IEEE Signal Processing Letters, vol.25, no.9, pp.1423-1427, 2018.
T. Yasui, M. Kuribayashi, N. Funabiki, and I. Echizen
"Dynamic estimation of collusion strategy for the detection of colluders in fingerprinting codes,"
Technical Report of IEICE, EMM Sept., 2018.
T. Yasui, M. Kuribayashi, and N. Funabiki,
"Estimation of collusion strategy for fingerprinting codes,"
Technical Report of IEICE, EMM March, 2018. 2017 EMM Best Poster Award
M. Kuribayashi and N. Funabiki,
"Universal scoring function based on bias equalizer for bias-based fingerprinting codes," IEICE Trans. Fundamentals, vol.E101-A, no.1, pp.119-128, 2018.
Related results
T. Yasui, M. Kuribayashi, N. Funabiki, and I. Echizen,
"Near-optimal detector for binary Tardos code by estimating collusion strategy"
IEEE Trans. Information Forensics and Security, vol.15, pp.2069-2080, 2020.
The Telecommunications Advancement Foundation Student Award
T. Yasui, M. Kuribayashi, and N. Funabiki,
"Estimation of collusion strategy for fingerprinting codes under noisy environment,"
Technical Report of IEICE, EMM March, 2019. 2018 EMM Best Poster Award
M. Kuribayashi, "Bias-based binary fingerprinting code under erasure channel,"
IEEE Signal Processing Letters, vol.25, no.9, pp.1423-1427, 2018.
T. Yasui, M. Kuribayashi, N. Funabiki, and I. Echizen
"Dynamic estimation of collusion strategy for the detection of colluders in fingerprinting codes,"
Technical Report of IEICE, EMM Sept., 2018.
T. Yasui, M. Kuribayashi, and N. Funabiki,
"Estimation of collusion strategy for fingerprinting codes,"
Technical Report of IEICE, EMM March, 2018. 2017 EMM Best Poster Award
M. Kuribayashi and N. Funabiki,
"Universal scoring function based on bias equalizer for bias-based fingerprinting codes," IEICE Trans. Fundamentals, vol.E101-A, no.1, pp.119-128, 2018.














